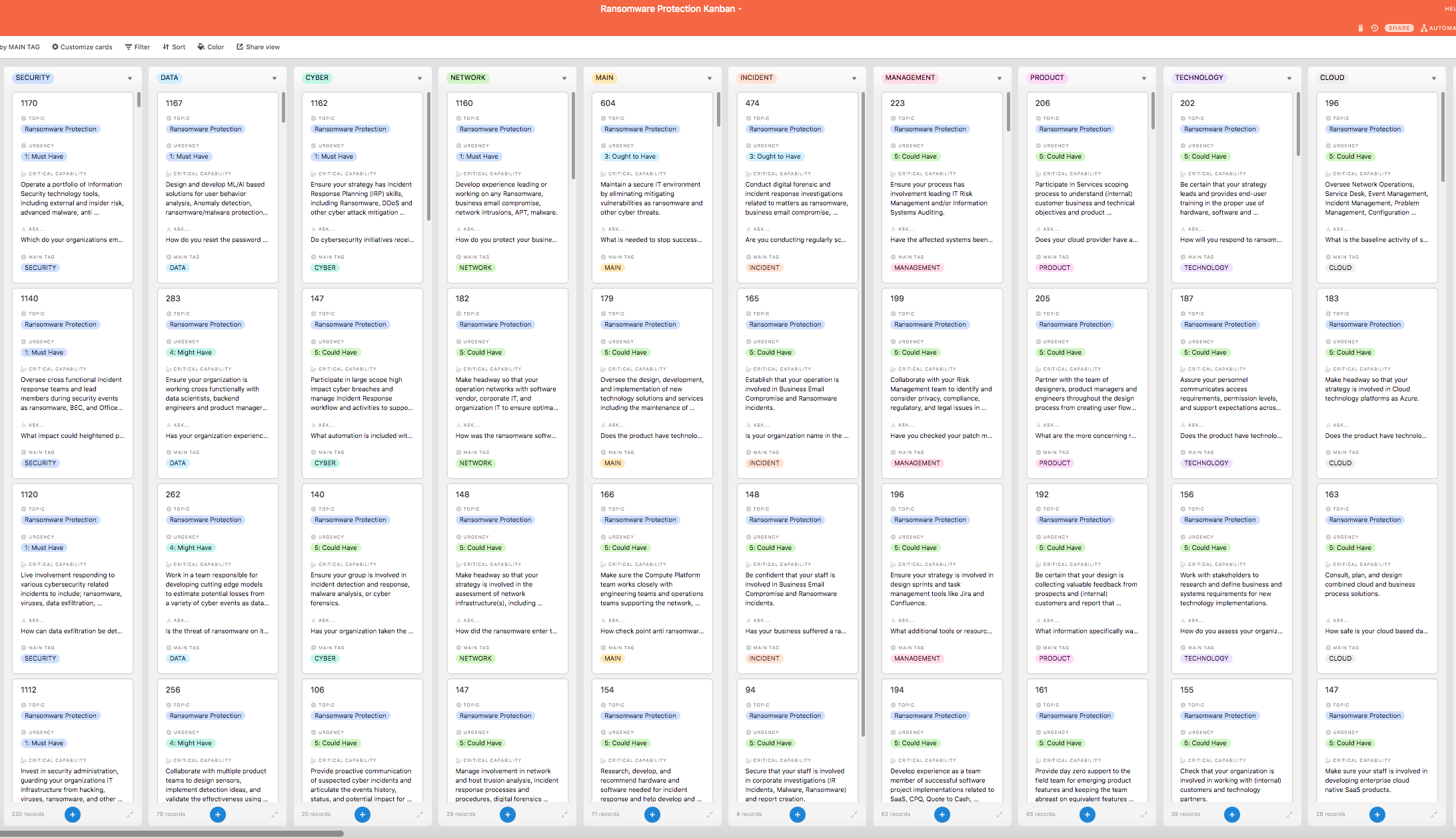
Look inside the Kanban:
https://theartofservice.com/Ransomware-Protection-kanban
Operate a portfolio of Information Security technology tools, including external and insider risk, advanced malware, anti ransomware, privileged access and dark web monitoring.
Benefits of the Ransomware Protection Kanban
- Coordinate vulnerability prioritization and patch management across security and IT.
- Maximize the value of your content and boost visibility and control over your sensitive data, while safeguarding your business from ransomware and insider threats.
- Assess your organizations current ability to either block or detect ransomware before it locks or encrypts data within your systems.
- Restrict the connectivity and Active Directory trust relationships between different areas of the business to slow down and limit the spread of ransomware attacks.
- Determine what data protection vendor best prepares you for a ransomware attack.
- Detect and stop insider threats, ransomware, data exfiltration and beyond.
- Prevent data theft from ransomware, malware, or trojan attacks.
- Provide consistent network security across remote locations.
- Assess your organizations level of user awareness to defend against ransomware attacks.
- Educate and validate that your users understand their role in cybersecurity.
Summary
The Art of Service has identified and prioritized 836 Ransomware Protection critical capabilities and use cases to assess and use. Leaders can select those results that best align with their business needs before implementing a solution.
The Art of Service's Critical Capabilities evaluates and prioritizes hundreds of results to help with the outcome selection process.
This Critical Capabilities Kanban will enable leaders to shortlist hundreds of appropriate results fast, because they are uniquely ready-to-use prioritized, starting with the 'Must Have' category; the most urgent and critical priorities.
This Kanban will help you plan and manage your Ransomware Protection roadmap.
- Transform the data into actionable views for your organization: business data changes, so how you view it should be flexible. Create the perfect view that's right for you.
- Put your workflows on autopilot: Help your team go faster and focus on what matters by automating your processes. Upload and use the Kanban with your favorite apps and services like Asana, Airtable, Basecamp, Monday.com, Atlassian, Trello etc.
- Knock down data silos: Align your teams around a single source of truth with real-time data from different sources. Point. Click. Stay in Sync.
- Use it's flexible reporting for your unique use case: Whether you're "no-code" or you "know-code", the Kanban is the foundational tool to show what you want to who needs to see it.
Included in your instant download purchase are the following digital products:
As seen in the Kanban above, the complete 836 Ransomware Protection critical capabilities and use cases, their prioritization, workflows, tagging and questions.
The download is available as an easy to re-use Excel format, which you can use as is, or import in any management tool of your choice, like Monday.com, Atlassian, Smartsheet, Power BI, Asana, Airtable etc.
Also included is the Ransomware Protection critical capabilities Book in PDF format covering all the criteria including ideas for (potential) roles to assign the criteria to. Table of contents:
About The Art of Service
Ransomware Protection Critical Capabilities, Meaningful Metrics And Their Prioritization
Background
Prioritization Of Requirements
The Prioritization Categories Are:
- Must Have
- Should Have
- Ought to Have
- Might Have
- Could Have
Use In New Product/Service/Process Development
Benefits
The Critical Ransomware Protection Capabilities And Their Priorities:
- Priority - Must Have #
- Priority - Should Have #
- Priority - Ought to Have #
- Priority - Might Have #
- Priority - Could Have #
Index
You're in good company. Join:
Trusted by: Capgemini, iknowvate technologies, KION Group AG, Cisco Meraki, Virginia Tech, Environmental Defense Fund, Abbott Laboratories, USAA, Datadog, Wells Fargo, Optiv, Azzur Group, Huntington Bank, PacifiCorp, John Deere, Biogen, AIG, The Ohio State University, Cloudflare, Ferguson, Netskope, PG&E Corporation, Federal Reserve Bank of New York, University of North Carolina at Chapel Hill, Agama Solutions, Wyze Labs, Barnes, Dennig & Co., Ltd., Eastman, Booz Allen Hamilton, DocuSign, S&P Global, Portland General Electric, Rockwell Automation, Hewlett Packard Enterprise, OhioHealth, Premier Staffing Partners, Harvard Pilgrim Health Care, Abbvie, KPMG, The Walt Disney Company (Corporate), LogMeIn, Liberty, CareJourney, Industrial Scientific Corporation, Weld County, CO, Principal Financial Group, TransUnion, Callaway Golf Company, Kemper, BD, Relias LLC, Blue Shield of California, LG&E and KU Energy, Chevron Phillips Chemical Company, Topgolf, PulteGroup, Honeywell, Federal Reserve Bank of San Francisco, Deutsche Bank, Humana, Premera Blue Cross, EMMES, RELATION INSURANCE INC, Nuvance Health, Verizon, University of Arizona Global Campus, Area 1 Security, Dataminr, Starbucks, Fairview Health Services, iHeartMedia, Inc., Palo Alto Networks, AT&T, Lutron Electronics, Infinity Consulting Solutions, Inc., International Data Group, Inc., Datto Jobs, Costco Wholesale, Blue Yonder, Norfolk Southern Corp, Amazon Data Services, Inc., Stifel Financial Corp., CitiusTech, Vouch Insurance, NTT DATA Business Solutions, Robinhood, ARM Treasure Data, Bravent, II-VI, Cincinnati Children's Hospital, Wayfair, StackPath, Match Group, Logitech, Lindsay, AlignTech, Cognosante, LLC, The Hanover Insurance Group, Paradigm, Carpe Data, Integrated Data Services Inc., Amazon.com Services LLC, LSEG (London Stock Exchange Group), Johnson & Johnson Family of Companies, Security PS, VMware, Walmart