Look inside the Kanban:
https://theartofservice.com/Threat-Management-Strategies-kanban
Administer and maintain security systems in the cybersecurity security operations center (CSOC) technology stack, including the security information and event management (SIEM) environment; OT and IT network intrusion detection systems (IDS); endpoint detection and response (EDR) tool; security orchestration, automation, and response (SOAR); cyber threat intelligence platform (TIP); and full packet capture (PCAP) servers across your service territory.
Benefits of the Threat Management Strategies Kanban
- Have you fully considered how cloud services and mobile working affects your risk and threat management models?
- Does your organization have a Threat Management Team (TMT) to conduct threat evaluations?
- Does your organization have a working, clearly defined security standards development process?
- What are the top 3 future challenges your organization will need to address regarding overall IT security threat management in the next two years?
- If your organization does not have forensic cyber threat analysis in-house, does local law enforcement have a resource?
- Does your organization have a defined insider threat management program that involves cooperation among multi disciplinary areas of your organization as human resources, IT and legal?
- Does your organization have integrated threat management and mitigation across client, server and edge?
- Does your system have inventory control procedures for access badges, uniforms, and equipment?
- Does your company have any routines about risk identification in conceptual design stages?
- How do threat management services help you measure your overall security effectiveness?
Summary
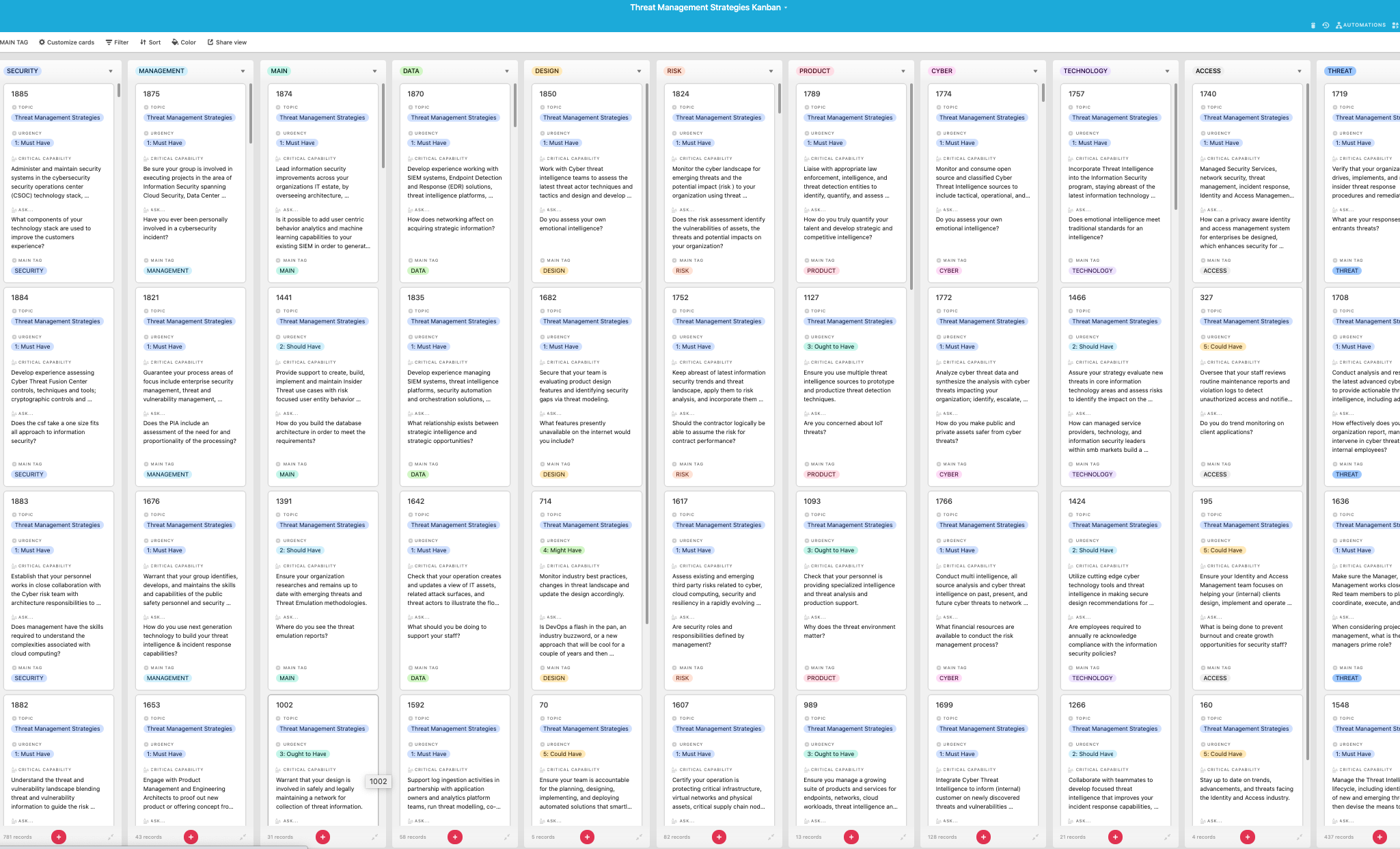
The Art of Service has identified and prioritized 1885 Threat Management Strategies critical capabilities and use cases to assess and use. Leaders can select those results that best align with their business needs before implementing a solution.
The Art of Service's Critical Capabilities evaluates and prioritizes hundreds of results to help with the outcome selection process.
This Critical Capabilities Kanban will enable leaders to shortlist hundreds of appropriate results fast, because they are uniquely ready-to-use prioritized, starting with the 'Must Have' category; the most urgent and critical priorities.
This Kanban will help you plan and manage your Threat Management Strategies roadmap.
- Transform the data into actionable views for your organization: business data changes, so how you view it should be flexible. Create the perfect view that's right for you.
- Put your workflows on autopilot: Help your team go faster and focus on what matters by automating your processes. Upload and use the Kanban with your favorite apps and services like Asana, Airtable, Basecamp, Monday.com, Atlassian, Trello etc.
- Knock down data silos: Align your teams around a single source of truth with real-time data from different sources. Point. Click. Stay in Sync.
- Use it's flexible reporting for your unique use case: Whether you're "no-code" or you "know-code", the Kanban is the foundational tool to show what you want to who needs to see it.
Included in your instant download purchase are the following digital products:
As seen in the Kanban above, the complete 1885 Threat Management Strategies critical capabilities and use cases, their prioritization, workflows, tagging and questions.
The download is available as an easy to re-use Excel format, which you can use as is, or import in any management tool of your choice, like Monday.com, Atlassian, Smartsheet, Power BI, Asana, Airtable etc.
Also included is the Threat Management Strategies critical capabilities Book in PDF format covering all the criteria including ideas for (potential) roles to assign the criteria to. Table of contents:
About The Art of Service
Threat Management Strategies Critical Capabilities, Meaningful Metrics And Their Prioritization
Background
Prioritization Of Requirements
The Prioritization Categories Are:
- Must Have
- Should Have
- Ought to Have
- Might Have
- Could Have
Use In New Product/Service/Process Development
Benefits
The Critical Threat Management Strategies Capabilities And Their Priorities:
- Priority - Must Have #
- Priority - Should Have #
- Priority - Ought to Have #
- Priority - Might Have #
- Priority - Could Have #
Index
You're in good company. Join:
Trusted by: Microsoft, CRI Advantage, Noblis, Booz Allen Hamilton, Netskope, FREEDOM CONSULTING GROUP, US Defense Threat Reduction Agency, McKinsey & Company, Area 1 Security, Fairview Health Services, Medtronic, Amazon Data Services, Inc., NTT DATA Business Solutions, Walmart, DataLink Fund Solutions, FireEye, Inc., Centene Corporation, HashiCorp, Wintrust Financial Corporation, Splunk, Huntington Ingalls Industries Inc., Raytheon Intelligence & Space, Assured Information Security, Inc. (AIS), McDonald's Corporate, Liberty Mutual Insurance, Northrop Grumman, Major League Baseball, DirectDefense, Lenovo, Synopsys, Netflix, Amazon.com Services LLC, Green Dot Corporation, PRICE WATERHOUSE COOPERS, Zelis, Deloitte, Sasol, Credit Suisse, TIAA, MKS2 Technologies, Contrast Security, IBM, Assa Abloy, Boston Scientific Corporation, Google, GE Healthcare, DSoft Technology, Engineering & Analysis, Morningstar, First Quality, Finastra, Amazon Dev Center U.S., Inc., William Hill US, PTC, Netlify, Dun & Bradstreet, Chargebee, Digital Defense, Inc., HCA Healthcare, San Antonio Water System, Uber, UST Global, Businessolver, Facebook, Raytheon Missiles & Defense, MassMutual, PepsiCo, Sonos, Inc, Foot Locker, Palindrome Technologies‚Äã, Pearl Technology, LLC, Oxide Computer Company, Citi, Apple, Tesla, Steampunk, Truist Financial, News Corp, VerSprite, Home Depot / THD, United Airlines Inc., Kraft Heinz Company, Teach For America, Amex, Lettuce Entertain You Restaurants (Chicago), Tanium, ShipBob Inc, The Walt Disney Company (Corporate), Intel