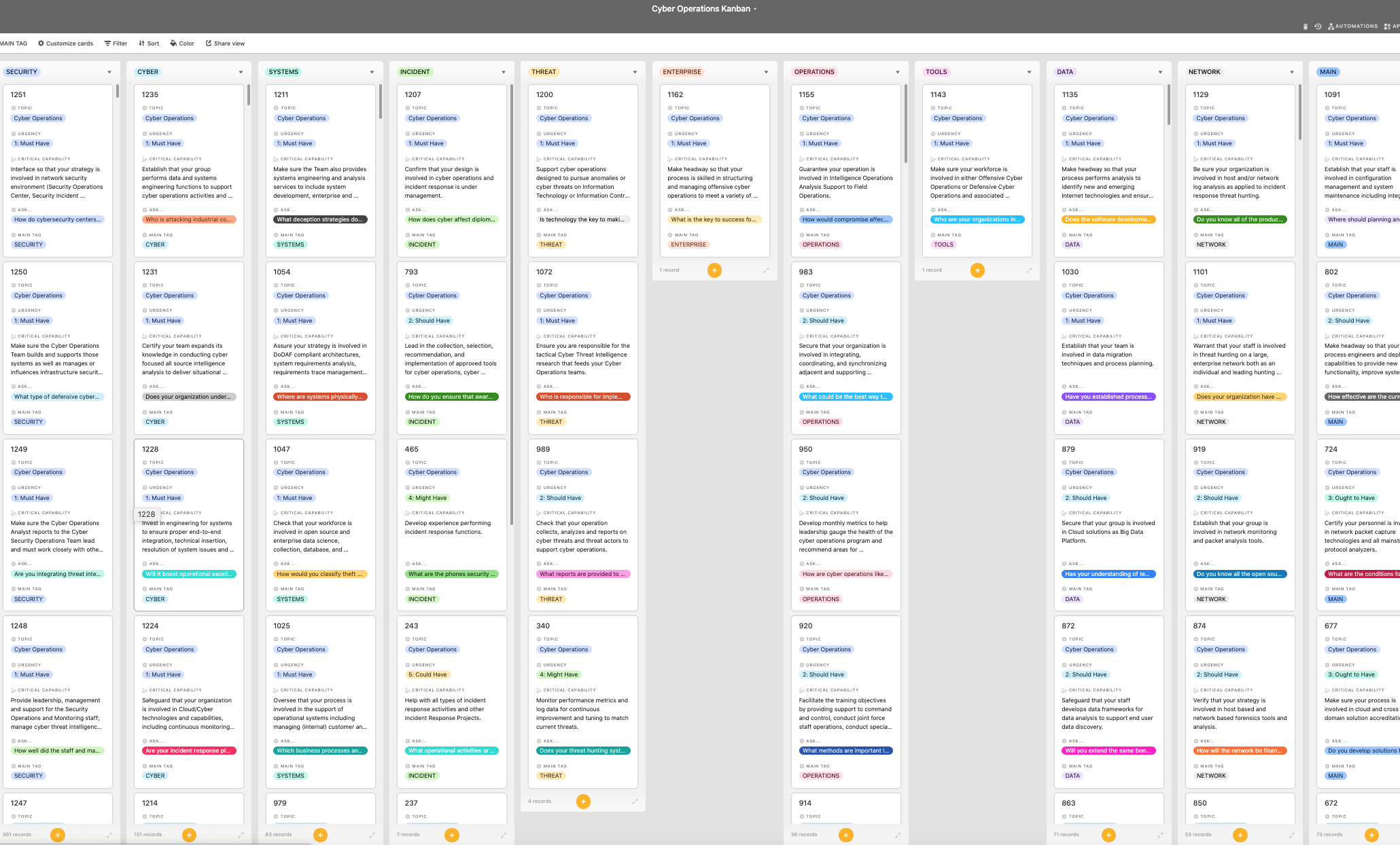
Look inside the Kanban:
https://theartofservice.com/Cyber-Operations-kanban
Lead so that your strategy is involved in network security environment (Security Operations Center, Security Incident Response Team, or Cyber Security Incident Response) investigating targeted intrusions through complex network segments and certify your company is involved in operational technology engineering and security concepts.
Benefits of the Cyber Operations Kanban
- If you have a large scale cyber attack that leads to infrastructure damage and you are is called in to assist, what organization department will take the lead?
- What critical information does the cyber criminal already have on your organizations operations?
- Instead of each Service developing redundant capabilities at great expense, would it make more sense to have a consolidated cyber corps as its own Service?
- What implications do vendor relationships have for command and control arrangements, accountability and defining rules of engagement in cyber operations?
- Does Cyber Command have the resources and the expertise to at least produce operational requirements?
- Do you have adequate all source and multi intelligence fusion and analysis capabilities for cyber to support the cyber mission teams you are building?
- Does your organization exercise and prepare its cyber/ network defense capabilities enough to address the risk posed by a cyber attack?
- What are offensive cyber operations and why do they matter?
- What level of impact must an incoming cyber attack have to justify active threat neutralization?
- Will the shift of employees from other programs to Cyber Operations cause a revenue lost for those programs?
Summary
The Art of Service has identified and prioritized 1251 Cyber Operations critical capabilities and use cases to assess and use. Leaders can select those results that best align with their business needs before implementing a solution.
The Art of Service's Critical Capabilities evaluates and prioritizes hundreds of results to help with the outcome selection process.
This Critical Capabilities Kanban will enable leaders to shortlist hundreds of appropriate results fast, because they are uniquely ready-to-use prioritized, starting with the 'Must Have' category; the most urgent and critical priorities.
This Kanban will help you plan and manage your Cyber Operations roadmap.
- Transform the data into actionable views for your organization: business data changes, so how you view it should be flexible. Create the perfect view that's right for you.
- Put your workflows on autopilot: Help your team go faster and focus on what matters by automating your processes. Upload and use the Kanban with your favorite apps and services like Asana, Airtable, Basecamp, Monday.com, Atlassian, Trello etc.
- Knock down data silos: Align your teams around a single source of truth with real-time data from different sources. Point. Click. Stay in Sync.
- Use it's flexible reporting for your unique use case: Whether you're "no-code" or you "know-code", the Kanban is the foundational tool to show what you want to who needs to see it.
Included in your instant download purchase are the following digital products:
As seen in the Kanban above, the complete 1251 Cyber Operations critical capabilities and use cases, their prioritization, workflows, tagging and questions.
The download is available as an easy to re-use Excel format, which you can use as is, or import in any management tool of your choice, like Monday.com, Atlassian, Smartsheet, Power BI, Asana, Airtable etc.
Also included is the Cyber Operations critical capabilities Book in PDF format covering all the criteria including ideas for (potential) roles to assign the criteria to. Table of contents:
About The Art of Service
Cyber Operations Critical Capabilities, Meaningful Metrics And Their Prioritization
Background
Prioritization Of Requirements
The Prioritization Categories Are:
- Must Have
- Should Have
- Ought to Have
- Might Have
- Could Have
Use In New Product/Service/Process Development
Benefits
The Critical Cyber Operations Capabilities And Their Priorities:
- Priority - Must Have #
- Priority - Should Have #
- Priority - Ought to Have #
- Priority - Might Have #
- Priority - Could Have #
Index
You're in good company. Join:
Trusted by: Eli Lilly, Humana, Mazars USA, Azzur Group, CRI Advantage, Noblis, Huntington Bank, PacifiCorp, John Deere, Booz Allen Hamilton, Boston Scientific Corporation, Honeywell, University of Arizona Global Campus, Fairview Health Services, National Renewable Energy Laboratory, Johnson & Johnson Family of Companies, Walmart, XIFIN, Acquired Data Solutions, Capital One, Deloitte, University of Colorado, Avaya, NJ Transit, Cisco Systems, GE Healthcare, Nike, PDI, Central Intelligence Agency, Advanced Micro Devices, Inc., Elliott Davis, NielsenIQ, Centene Corporation, BNY Mellon, SBG Technology Solutions, Wells Fargo, OneNeck IT Solutions, Abbott Laboratories, FICO, Zebra Technologies, SharkNinja, Fishtech Group LLC, Levi Strauss & Co., Optiv, Hillenbrand, Inc., EY Global Services Limited prod, Texas Capital Bank, West Monroe Experienced, Coalfire, Visa, Harris County, BlackRock, FedEx Services, USAA, GE Corporate, Albertsons Companies, Coca-Cola Bottling Company Consolidated, GovernmentCIO LLC, Home Depot / THD, Marsh, AIR, System Services, JANUS Research Group, Hudson MX, Boecore, US Federal Deposit Insurance Corporation, Systems X, Motorola Solutions, Abrigo, General Dynamics Information Technology, B&V Pathway Forensics, IDENTIFY SECURITY, Rule4, AirBorn, Evolve Security, Moss Adams, Raytheon Intelligence & Space