Look inside the Kanban:
https://theartofservice.com/Network-Security-kanban
Make sure the Information Assurance Analyst works in a shift work environment that requires security minded individuals with good understanding network security posture and network security tools including firewalls, intrusion detection and prevention technology, threat and vulnerability management tools, data loss prevention tools, filtering technologies, traffic inspection solutions, reporting technology, audit reduction and report generating tools, and data analytics platforms.
Benefits of the Network Security Kanban
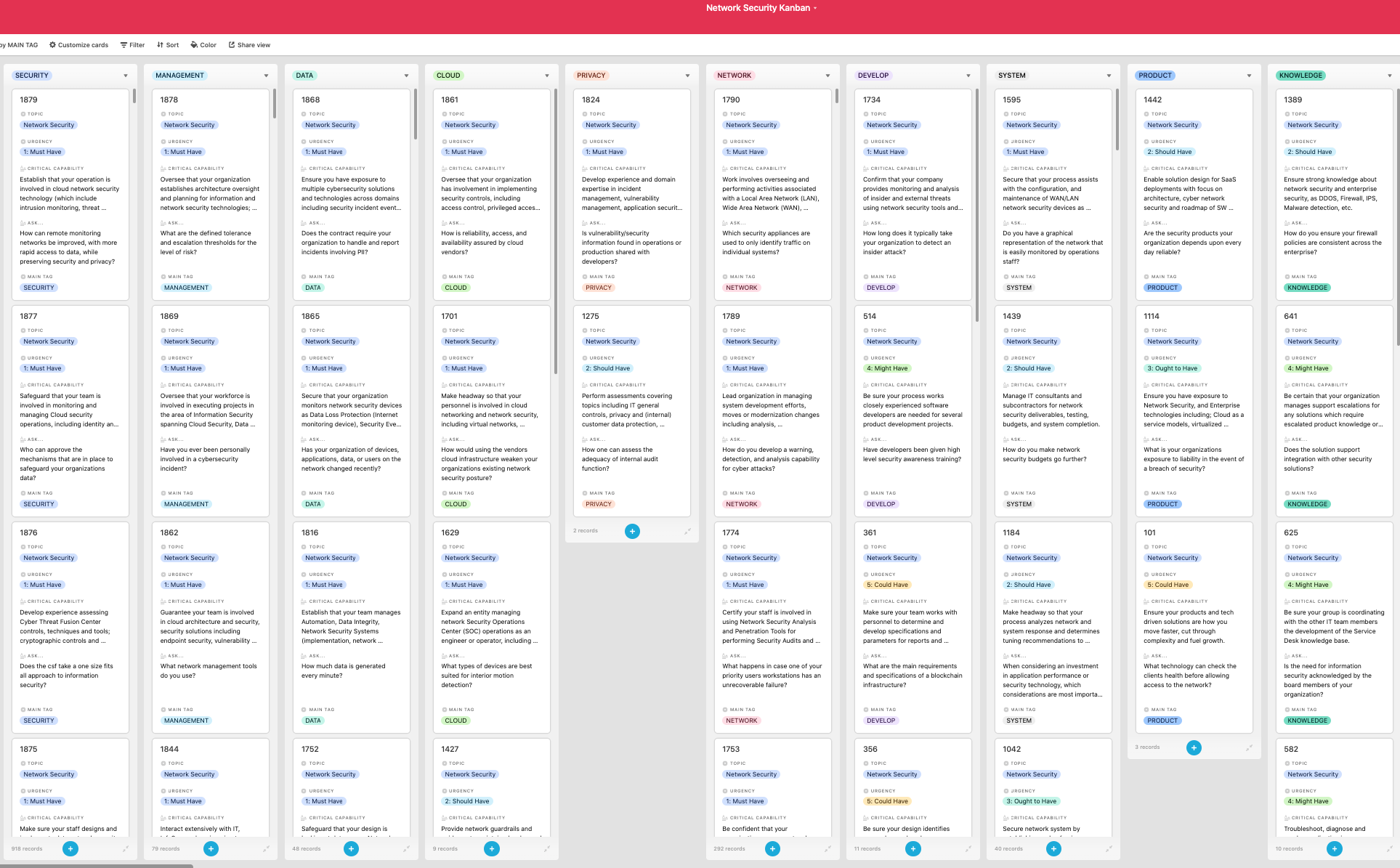
- Is your organization logging any network events that would allow you to determine if a data security breach may have occurred?
- Do you have insight in regular updates that shows all the latest security patches and the status of every machine on your network so you know your systems have been secured and updated?
- Where business partners and/or third parties need access to information system is the network segregated using perimeter security mechanisms as firewalls?
- To what extent has your organization implemented security controls to prevent data exfiltration and enhance network defenses?
- Is a base network stack satisfactory (for a system locked in a secure area for example), or does a full featured network stack with a complete security portfolio make more sense?
- Do your staff members have appropriate awareness, knowledge and skills to maintain the security of the network and information systems that support your delivery of essential services?
- What wireless network security controls do you have in place to secure your network from hackers sitting in your parking lot and capturing your data?
- Does your organization have a process to verify security policy compliance of all network connected devices?
- Which technology and business factors does your organization use to structure network based security strategies?
- Do your security systems detect insider misuse, misconfigured devices and unauthorized attempts to access internal network resources in real time?
Summary
The Art of Service has identified and prioritized 2005 Network Security critical capabilities and use cases to assess and use. Leaders can select those results that best align with their business needs before implementing a solution.
The Art of Service's Critical Capabilities evaluates and prioritizes hundreds of results to help with the outcome selection process.
This Critical Capabilities Kanban will enable leaders to shortlist hundreds of appropriate results fast, because they are uniquely ready-to-use prioritized, starting with the 'Must Have' category; the most urgent and critical priorities.
This Kanban will help you plan and manage your Network Security roadmap.
- Transform the data into actionable views for your organization: business data changes, so how you view it should be flexible. Create the perfect view that's right for you.
- Put your workflows on autopilot: Help your team go faster and focus on what matters by automating your processes. Upload and use the Kanban with your favorite apps and services like Asana, Airtable, Basecamp, Monday.com, Atlassian, Trello etc.
- Knock down data silos: Align your teams around a single source of truth with real-time data from different sources. Point. Click. Stay in Sync.
- Use it's flexible reporting for your unique use case: Whether you're "no-code" or you "know-code", the Kanban is the foundational tool to show what you want to who needs to see it.
Included in your instant download purchase are the following digital products:
As seen in the Kanban above, the complete 2005 Network Security critical capabilities and use cases, their prioritization, workflows, tagging and questions.
The download is available as an easy to re-use Excel format, which you can use as is, or import in any management tool of your choice, like Monday.com, Atlassian, Smartsheet, Power BI, Asana, Airtable etc.
Also included is the Network Security critical capabilities Book in PDF format covering all the criteria including ideas for (potential) roles to assign the criteria to. Table of contents:
About The Art of Service
Network Security Critical Capabilities, Meaningful Metrics And Their Prioritization
Background
Prioritization Of Requirements
The Prioritization Categories Are:
- Must Have
- Should Have
- Ought to Have
- Might Have
- Could Have
Use In New Product/Service/Process Development
Benefits
The Critical Network Security Capabilities And Their Priorities:
- Priority - Must Have #
- Priority - Should Have #
- Priority - Ought to Have #
- Priority - Might Have #
- Priority - Could Have #
Index
You're in good company. Join:
Trusted by: GCI, Microsoft, Barnes, Dennig & Co., Ltd., E&M Technologies, Hurricane Electric, Peraton, Cognosante, LLC, Booz Allen Hamilton, Amazon.com Services LLC, University of North Texas System, General Dynamics Information Technology, Intel, Nexstar Network, Palo Alto Networks, Matrix Medical Network, AT&T, LTS, Honest Networks, Benu Networks, WellSky, TekSynap, Security PS, Boston College, Databricks, Bigleaf Networks, Amazon Data Services, Inc., WSSC Water, Amazon Web Services, Inc., Juniper Networks, Ukpeagvik Iñupiat Corporation/Bowhead Family of Companies, Arista Networks, KGI Wireless, Lumen, Trova, Intone Networks, Charles Schwab, Invesco, The Intellekt Group, The Hershey Company, MetLife, Carilion Clinic, CodeBlue, Network N, National Network of Public Health Institutes (NNPHI), Farmer's Business Network, Inc., Homeland Security and Emergency Services, Division of, U.S. Navy, US Federal Housing Finance Agency, University of Wisconsin–Madison, IntelliGenesis, LLC, Invictus Associates, System Services, First Commonwealth Bank, Wintrust Financial Corporation, Raytheon Intelligence & Space, Information Technology Services, Office of, American Transmission Co., Louisiana-Pacific Corporation, ‚Äö√Ñ√£Markesman Group, Sabre, DEPT OF INFO TECH & TELECOMM, Alliance Health, Splunk, JANUS Research Group, Hudson MX, Plaid, Boecore, US Federal Deposit Insurance Corporation, Systems X, Cognizant Technology Solutions, Mattel, Armison Tech, Farm Credit Bank of Texas, CACI, Motorola Solutions, Electronic Systems, Inc., Protiviti, Abrigo, PassionHR, OPS Consulting, LLC, Huntington